Describe 3 Techniques Used by Hackers to Breach Networks
Usually theyre motivated by both as uncovering a wealth of data can help them to cash in. According to the report attackers commonly used malware to compromise a host but turned to legitimate tools once inside the network.

5 Password Cracking Techniques Used By Hackers
Larger advertisers like Facebook and Google have a number of safeguards in place to prevent this behavior but even they arent 100 perfect.
. Still there are similar strategies and tactics often used in battle because they are time-proven to be. Hackers are usually after two things from your business. Fences and gates.
Use a virtual private network VPN Conduct proper maintenance. One of the best ways to foil breach attempts is to update your operating system and all application software as the new versions have most likely been fine tuned to prevent. There are different types of network attacks and prevention techniques which are described as below.
With technology getting advanced the phishing techniques being used are also getting more advanced. Use IDSIPS to track potential packet floods. UI Redress DNS Spoofing Brute Force are among the common hacking techniques.
24x7x365 Monitoring Leverage 24x7x365 monitoring to. Moreover the report shows that Angry IP Scanner an. Structured query language SQL code injection.
Risk Assessments Assess your current IT infrastructure to identify threats and vulnerabilities and reduce risk. Fuzzing is a popular technique used by hackers to probe for software vulnerabilities in a network service. It can record phone conversations.
Following are some phishing technologies being used. Database sites and applications are particularly vulnerable to SQLI attacks since they are designed to allow searchability and. Read this article by Techfunnel to know more such latest hacking techniques.
The most common method for hackers to spread ransomware is through. Once youve clicked on the ad the. Somewhere along the chain of events that begins with the user taking the bait the fraudsters will present a fake login form to steal the users login name and password.
These are the four most common ways ransomware infects its victims. Phishing via iCloud and Gmail account was the attack route taken by hackers who targeted the Fappening leak which involved numerous Hollywood female celebrities. It can be used to send SMSs to premium-rate numbers and drain out your balance.
If youve ever studied famous battles in history youll know that no two are exactly alike. Network analysers are tools that allow hackers to monitor and intercept data packets sent over a network and lift the plain text passwords contained. This is a random testing in which the target is fed with.
Web attacks 18 Cybercriminals can extort website operators for profit sometimes by threatening to steal client databases or shut down the website. A computer virus is a software program that can. Compromised data can cost.
If you consider a graph where the x-axis lists all of the devices and apps on your network infrastructure apps endpoints IoT etc and the y-axis are the different breach methods such.

What Is Hacking Types Of Hacking More Fortinet
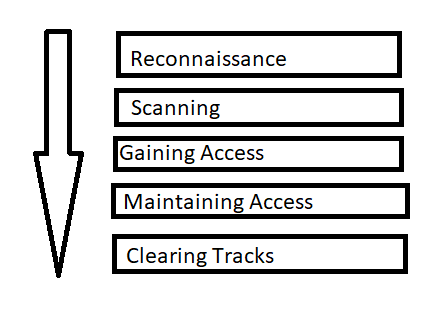
Phases Of Hacking Ethical Hacking

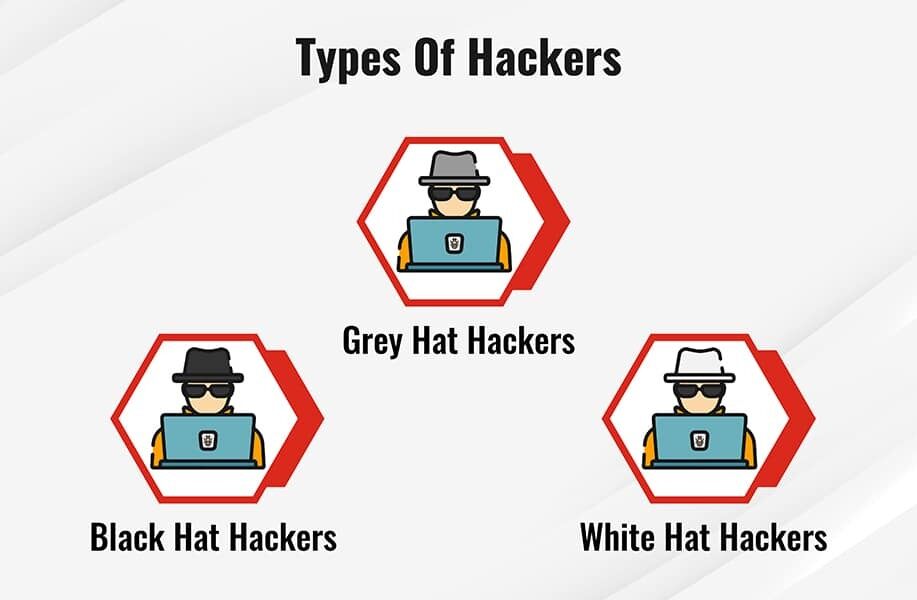
Types Of Hackers Maryville Online

8 Common Hacking Techniques That Every Business Owner Should Know About

Comments
Post a Comment